Aplikasi Hack Proxy Server
Per App Hacking is one of the best Xposed Framework modules. It can be used to make changes to how apps work on a case by case basis, making them more battery efficient and even getting them to run automatically through a proxy.
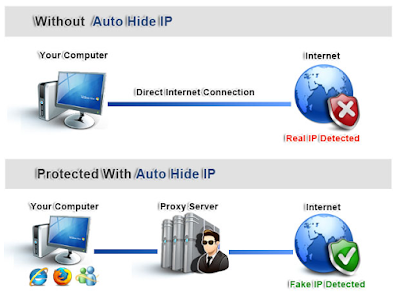
Mengganti Proxy VPN memiliki fungsi yang cukup banyak ya seperti untuk menjaga privasi ataupun mengakses kembali server yang sebelumnya terkena banned IP *biasanya kalangan gamers nakal, kali ini saya akan membagikan cara mengganti VPN keseluruhan internet dalam satu komputer menggunakan sebuah aplikasi bernama. Seorang klien terhubung ke server proxy. Cara hack Belajarlah. Sebuah aplikasi proxy umum adalah proxy web cache. Server Connection and Operation Status Display UltraSurf Interface displays the status of server connection and operation. If the user has entered a proxy server on IE, that proxy server will not be used; it will. Cara Hacking Lan ( m4e5tro ).
In this tutorial we’ll show you how to set up and use Per App Hacking, and also guide you through its features and how to use them.
Install and activate the Per App Hacking module
Before you begin you’ll need to have rooted your device and got the Xposed Framework installed. Read our full guide on how to do this, if you’re not sure.
Now install the Per App Hacking module. Open the Xposed Installer app, tap Download and scroll down to Per App Hacking (or tap the search icon and type in the name).
You & I by The Dig, released 22 October 2013 1. You And I Lost Control 4. Via the free Bandcamp app, plus high-quality download in MP3, FLAC and more. 'Just Between You and Me' is Porter Wagoner & Dolly Parton's first duet album, released in January 1968, shortly after Parton joined Wagoner's band and. Nov 21, 2017 - “You In Me” is a title track recorded by South Korean co-ed group K.A.R.D (카드). It was released on November 21, 2017 by DSP Media. You and me flac danzig. Download You & Me by Meute at Juno Download. Listen to this and millions more tracks online.
Tap Per App Hacking and swipe across to the Versions tab. Tap Download on the latest version.
The module will download and install. A notification will appear in the notification pane saying the module is not activated. Tap Activate and reboot to complete the install process.
Get started with Per App Hacking
Once your device reboots locate the Per App Hacking icon in your app drawer and tap it to launch.
The main screen for the Per App Hacking app contains three tabs. The first is All Apps, which shows all the apps installed on your phone or tablet.
The second is Enabled Apps, which lists those apps that you have modded. It will be empty at first.
The third tab is Backup/Restore. In this tab you can save your customisation settings and restore them. It’s a global backup covering all your hacked apps, and you cannot create backups on a per app basis.
To begin hacking your apps, pick one from the All Apps list. You’ll see the same set of options for each app.
Enable Proxy
This option enables you to run certain apps through a proxy server automatically.
An example use for this would be to bypass region locks within certain apps, such as a streaming media service not available in your country.
The app needs to use org.apache.http.impl.client.DefaultHttpClient, which is one of the http clients available in Android. Since this available is not freely available you can only test apps on a trial and error basis.
You’ll also need to enter details for your Proxy Host and Proxy Port. You can find lists of free proxy servers online; performance may vary wildly across them.
Time Machine
With Time Machine you can enter a fake time the app will read instead of the system time.
This could be used for apps use time restrictions (although note that many games will pull their time from the server they connect to rather than the OS, so you cannot use it skip the wait times in games like Star Wars: Commander).
To use Time Machine you need to enter the date and time in the box in the format YYYY-MM-DD HH:MI (e.g. 2014-09-25 12:53).
Limit Bitmap Dimensions
This option limits the size of an image to no more than the size of the screen in apps where this may be an issue.
Force to mute the MediaPlayer if silent in Profile Group
This is an option for CyanogenMod ROMs only. Some apps continue to sound their notifications even when the Silent profile is activated in CM ROMs.
Ticking the box of this option will ensure all your apps stay silent when they should.
Prevent Service
This useful setting prevents apps from launching until you explicitly launch them.
If you have an app you rarely use but that launches when you boot your phone, enable this setting to prevent it form launching.
Don’t use the option for apps you need running, such as messaging apps that will update in the background.
Prevent Wake Lock
Another useful option, Prevent Wake Lock stops an app from acquiring wakelock. Wakelock prevents your device from entering deep sleep, and can be major cause of battery drain.
You can identify apps that are misbehaving with a tool such as Wakelock Detector. When you find some that are preventing your device from sleeping, tick the Prevent Wake Lock box for the app in Per App Hacking to see if that solves the problem.
Prevent Alarm
Prevent Alarm is another battery saving setting.
Not related to the alarm clock function, an alarm for an app is when it is scheduled to wake for some reason.
Most apps that run in the background will do this. If you set your Twitter client, for example, to check for timeline updates every 30 minutes, the alarm function will be used to ensure the app wakes on schedule to carry out that task.
Helvetica neue lt arabic font free download. Often apps will need to use the function without any user input, and the presence of alarms shouldn’t be seen as a negative thing.
But some apps can misbehave, either malfunctioning or being overeager in their use of alarms and background resources.
Again, you can use Wakelock Detector (below) to identify a pattern between alarms and battery drainage.
If you identify an app that is using too many alarms, tick the Prevent Alarm box in Per App Hacking.
Proxy Hack Client
Next, tap Alarm Multipler. Selecting Ignored will ignore alarms entirely (and may prevent an app from functioning as expected).
Alternatively, pick a multiplier from x2 to x100. This reduces the number of alarms the app uses during by the number you choose. For instance, if an app used 30 alarms during a set period of time, the multiplier x30 would reduce it to just one alarm during the same period.
Be careful how you use this option, as it can have unexpected effects on how apps perform.
The benefits of Per App Hacking
The final three options on this list are the main strengths of the Per App Hacking module.
With these you can really reign in any apps that are using too many resources or draining your battery too quickly.
The module is safe to experiment with, and all the changes can be undone without any adverse effects.
We recommend making small changes at a time and testing their effects, rather than making lots of big tweaks all at once. Rebooting is also useful to ensure your changes are applied to the apps you are hacking.
Today, I will present the method of bypass the proxy server based on Squid. I was able to implement several bypasses using presented techniques. I will present ways of bypassing security’s weak (HTTP tunnels) and methods requiring the user computer knowledge (TSOCKS). As you know, nobody likes burglaries. The presented results, can be used for improving the quality of services, them security, patching security holes, blocking and filtering network disorderly traffic.
Proxy Site
Download si play app. Recently, large corporations and small companies began to stand on security the storage data and maintenance of network infrastructure in usable condition. Nowadays, we take Internet even with each other on mobile phones. Reliability in access to information has a specific priority and is very highly regarded in the IT market. Most of us also want to supervise data, which are sent to the network. Especially at corporate levels, managers and directors want to eliminate private traffic during working hours. They decided to block employees access to e.g. social networks or p2p type of Web2.0 websites. Sometimes used, popular traffic restrictions based on pipes (pipe) gave us the possibility of blocking unwanted ports. The next step is to block specified web-apps. This type of treatment of network traffic is used by proxy servers. The most popular of them is a Squid. It is a server for HTTP, HTTPS, FTP and other similar. It is used for reducing bandwidth and improving the response time by caching and reusing frequently called web pages. The configuration of this tool is done by entering rules to /etc/squid/squid.conf file. The next step is a configuration of the ACL list of denied and allowed addresses.
Tunnels on the HTTP Web
Comments
comments